
Android Devices Can Be Exploited With Decades Old Telephone Tech

How To Tell Compelling Stories While Avoiding Exploitation Nten
Exploiting The Exploited Quadrant Online
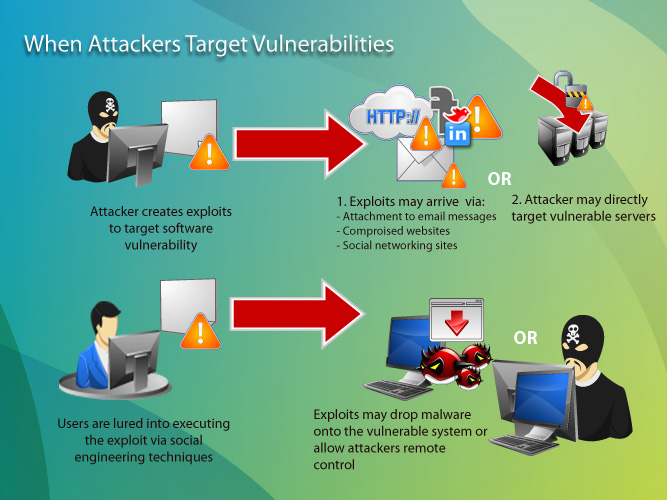
Exploit Definition Trend Micro Usa

Us Government And Business Are Systematically Defrauding And